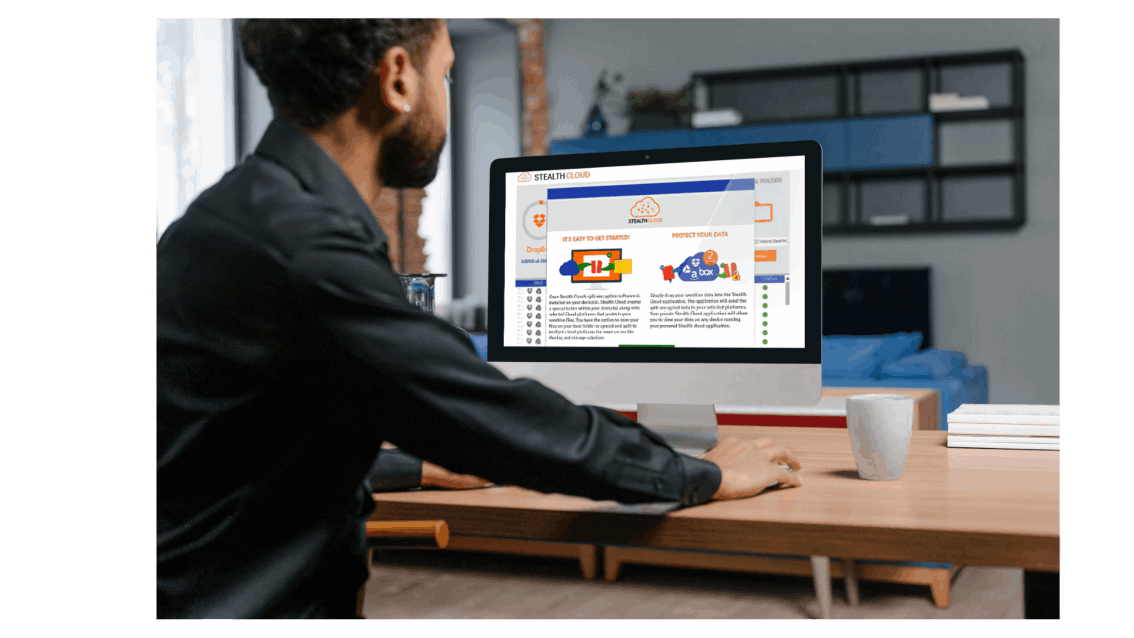
Unwavering Protection for Your Precious Data & Applications, Regardless of Location!
Unwavering Protection for Your Precious Data and Applications, Regardless of Location.
Expand and amplify the battle-proven cloud end-to-end split encrypted security and threat intelligence prowess of Stealth Grid to envelop public clouds and your internal IT environments.
Rest assured that your valuable assets are consistently shielded wherever they may reside.